0mega leaked popular IT Risk Monitoring Service “NEXTLABS”!
Recently Nextlabs, who is a pioneer in Data Security and Risk Management Service has been infected by 0mega Ransomware and 100% of their data which is sized about ~300GB; has been publicized on their Data Leak Site on 3rd October, 2022.

ABOUT THE LEAK
The leak consists of various sensitive information such as Employee Details, Financial Budgeting, Consulting License Agreements, Insurance Details, StockHolder Reports, Softwares etc.
The below screenshot indicates the data is freshly compromised as its “Effective Date” is recorded as July 2022.
Here are some of the leaked files, dated this year!
FINANCIAL DETAILS
It is important to note that the actor had leaked highly sensitive financial data of the company where the annual Cash Flow is listed.
Getting hold of these kinds of data helps the competitor to analyze the financial position of the company without guessing any estimation.
EMPLOYEE DETAILS
Generally, employees’ data are shredded once they no longer exist in the company. But however, it is shocking to find the personal data of Ex-Employees available at the firm. Following are the data of ex-employees which are found in the leak, indicating the being a “DATA SECURITY” company, it had not followed stringent policies.
It is also important to note here that the leak also consists of Vital Information such as Signature of CEO, as any attacker who holds this data could maliciously use it for masquerading purposes.
It also includes a sensitive SCREENSHOTS section, such as Client Names, Contracts Agreements, How it Works (Software Walkthrough), Source Codes etc.
List of NETXLABS Clients
This could also allow attackers to know the internals used by other companies, who rely on NEXTLABS, for their security practices.

ABOUT 0MEGA RANSOMWARE
This ransomware initially appeared in the month of July, 2022 and uses Double Extortion Techniques like other Ransomware Groups. Upon infection, all the victims’ files are encrypted and appended the extension .0mega to the infected files.
It can be assumed that the group had used Spear Phishing Campaigns or Malspams to compromise their victims via MS Office, as it is a common tactic used by Ransomware Operators along with RDP Disclosures to target their victims.
Currently, there are only 2 leaks found in their site, which are 450GB in total. Previously, the group had targeted a small Electronics Repair Firm based in the UK in the month of May, 2022.
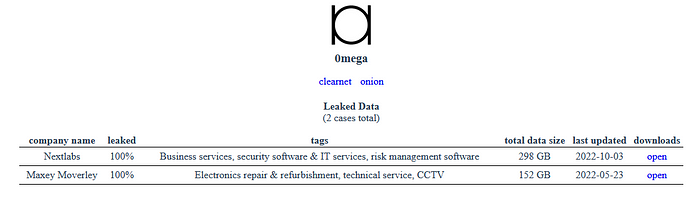
It is interesting to note that the 0mega had leaked (whole) 100% files of Maxey Moverley (initial victim) on 23rd May, 2022 at single go. But in the case of Nextlabs; the operators had split the data breach in 3 time frames, allowing enough time for the company to respond/negotiate to their ransom demand.
10% leaked on 15th September, 2022: 29.9GB
60% leaked on 27th September, 2022: 137.1GB
100% leaked on 3rd October 2022: 298GB
From this, it can be assumed that Threat Actors had spent 18 days on their second victim.
HOSTING DETAILS
Just like other ransomware groups, there are 3sites. 1 is used for Clients to get in touch with Team 0mega and other as Data Leak Site and the other is TOR version of leak site.
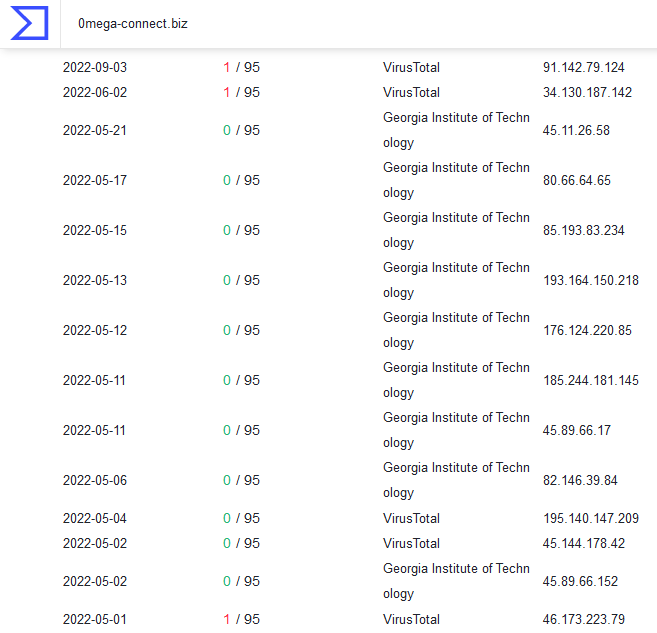
Client Helpdesk: 0mega-connect.biz
Data Leak Site: 0mega.cc
Onion: omegalock5zxwbhswbisc42o2q2i54vdulyvtqqbudqousisjgc7j7yd.onion
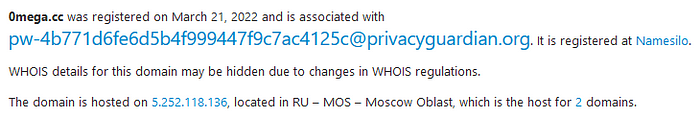
Tracing their domain details, it is found that they have registered their domain names in March 2022, which is hosted in Moscow.
By tracing the Certificate History, following are found:-
0mega-connect.biz: 94.103.83.128
Registered: 25th March, 20220mega.cc: 5.252.118.136
Registered: 21st March, 2022Domain Registrar: NameSilo
Hosted: AEZA Group NL
Server: nginx
OS: Ubuntu
ASN: AS210644
Suspected: 8GB RAM VPS running AMD Ryzen 9
While tracking the historical SSL Certificate details, it is found that 0mega-connect.biz was hosted with 89.223.127.196 which is hosted with Russian provider Timeweb.

As Timeweb is located in Moscow, it can be extrapolated that this is the right infrastructure.
NOTE:- There are sometimes multiple infrastructures related to a single entity. Hence, it is vital to inspect each IOC to get an in-depth understanding of the entities.
Here are some of the info found including hosting IP Blocks:-
0mega.cc
========
5.252.118.136
94.103.83.128
104.196.99.215
46.173.223.184
95.161.129.101
46.173.223.149
185.185.69.38
176.124.211.93
34.91.228.43
91.142.79.124
34.130.187.142
185.185.71.36
141.8.199.56
46.161.1.32
0mega-connect.biz
================
94.103.83.128
104.196.99.215
46.173.223.184
95.161.129.101
185.185.69.38
176.124.211.93
34.91.228.43
91.142.79.124
34.130.187.142
45.11.26.58
80.66.64.65
85.193.83.234
193.164.150.218
176.124.220.85
185.244.181.145
45.89.66.17
82.146.39.84
195.140.147.209
45.144.178.42
45.89.66.152
46.173.223.79
91.224.22.229
94.228.125.92
212.193.50.111
45.8.124.54
45.10.244.51
185.185.71.36
188.127.235.236
194.87.106.38
91.238.105.36
91.238.105.110
194.36.191.93
79.133.56.15
47.254.172.61
Add these IPs to your Blacklist in order to block any malicious activities!From the above IPs, it is interesting to note that most of the resolvers of 0mega-connect.biz are “Georgia Institute of Technology”.
POSSIBLE ASSOCIATION (Can’t Say!)
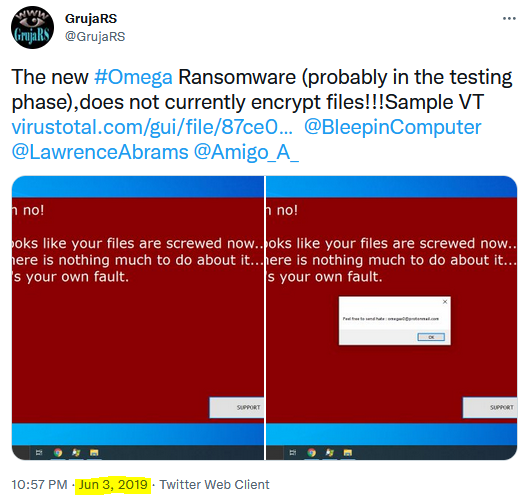
Upon Researching similar incident, it came to light that there was another Ransomware named “Omega” which was under development in June 2019. However, as the files were appended with extension “.dodger” it came to be known as Dodger Ransomware. The reason to call it Omega initially is because actors email address: omegax0@protonmail.com.
As per the tweet, it clearly shows that this ransomware is in the development stage and does not support Encryption.
It is observed that 0mega Ransomware Group is slow as compared to other counterparts, but they are improving gradually by improving their strategies. More information could be drawn after obtaining the ransomware samples.
Follow me on Twitter for interesting DarkWeb/InfoSec Short findings! ;-)
NOTE:- The article is purely an Individual Research and is not subjected to be used/published anywhere without the Author’s consent.
